- Published on
Using ASP.Net Forms Authentication on Load Balanced Servers
- Authors

- Name
- Jac Timms
We recently started using HAProxy to load balance between two application servers for both HTTP and HTTPS traffic. It was really easy to get working, has worked great so far and we’re really pleased with it. The only issue we had was with our login cookies, which are set via FormsAuth, as when logging in our visitors use HTTPS and might get a different server to the one they were ‘stuck’ to with HTTP which uses a cookie to ensure the same server. HAProxy can’t read a cookie from an SSL stream as the connection isn’t terminated at the proxy, it is still terminated at the web application server (you can end HTTPS connections at the proxy by installing a webserver on it as well though). For us this was an easy fix however.
From the Microsoft article on FormsAuth:
If you deploy your application in a Web farm, you must ensure that the configuration files on each server share the same value for validationKey and decryptionKey, which are used for hashing and decryption respectively. This is required because you cannot guarantee which server will handle successive requests.
With manually generated key values, the <machineKey> settings should be similar to the following example.
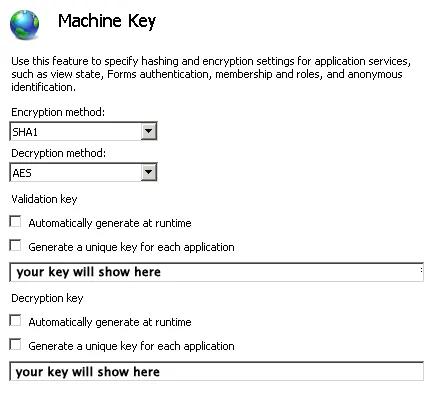
<machineKey validationKey="21F090935F6E49C2C797F69BBAAD8402ABD2EE0B667A8B44EA7DD4374267A75D7AD972A119482D15A4127461DB1DC347C1A63AE5F1CCFAACFF1B72A7F0A281B" decryptionKey="ABAA84D7EC4BB56D75D217CECFFB9628809BDB8BF91CFCD64568A145BE59719F" validation="SHA1" decryption="AES" />If you want to isolate your application from other applications on the same server, place the <machineKey> in the Web.config file for each application on each server in the farm. Ensure that you use separate key values for each application, but duplicate each application’s keys across all servers in the farm.
To generate a Machine Key, simply go to this handy webpage and generate a new key. You can then either add it just after the <system.web> element to your application’s local web.config or to the root web.config which will be in your .Net installation folder (something like C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config).
After you have done this on all your servers, you can check them all by going into IIS and selecting Machine Key where you can see if each server is using the correct keys.
However, after doing this it still wasn’t working for us. After a little digging about we realised we hadn’t installed any Windows Updates on the new server. I think it was specifically this one that was stopping it working, but after a full update and a reboot it all worked just fine.